Is it possible to uncover through search trends with which mathematical concepts are czech students struggling? I was trying for a while to do it, let me show you my findings and (limited) conclusions.
There are two main tools I’ve used for my tiny “research”. The first one is the Google Trends service provided by the most popular search engine worldwide today. The second tool is belonging to a more local search engine Seznam.cz, but having a great share (around 30 % back in 2016) in Czechia.
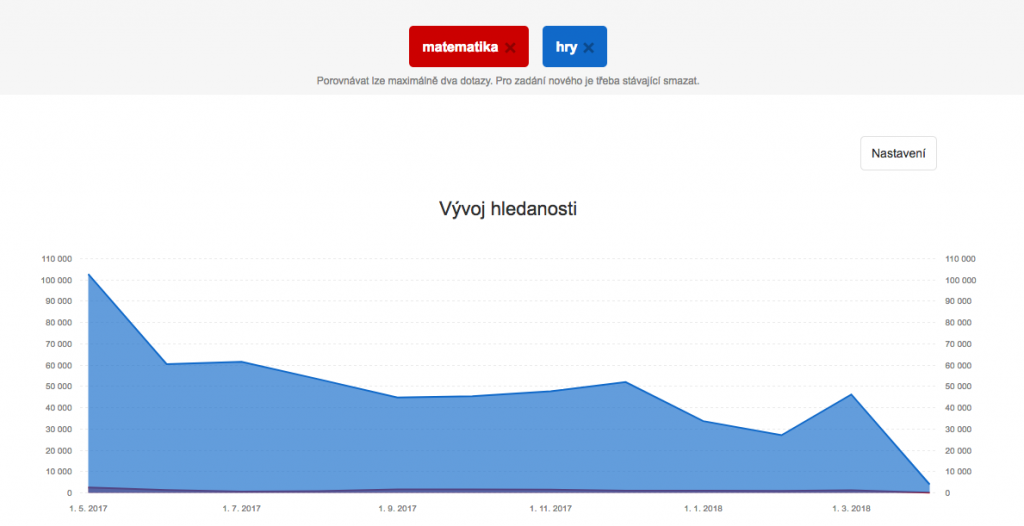
At first I was interested in how much and when is the term ‘matematika’ (= math) searched in general. The tool from Seznam shows the exact number of searches – it seems like the term is searched between 1 000 – 2 000 times per month with the exception of the summer months. A related term ‘matematika online’ (= math online) is searched similarly often. Even if we add those two it is still bit less than for example a searched term from different school subject ‘vyjmenovaná slova’ (grammatics of the Czech language). For another comparison a word ‘hry’ (= games) is being searched much more – in last two months it was searched 30 times more often than ‘math’. I’ve picked the ‘games’ for comparison as something pupils might be searching for. To put it in another perspective (to have some scale) let me pick as well a word from top 10 most searched keywords on the czech internet in 2016 – there is only one general word (not a name of a company or a service) and that is ‘porno’ (= porn). The ‘porn’ is being searched ten times more often than ‘games’, roughly 300 times more than ‘math’ on Seznam. Not surprising.
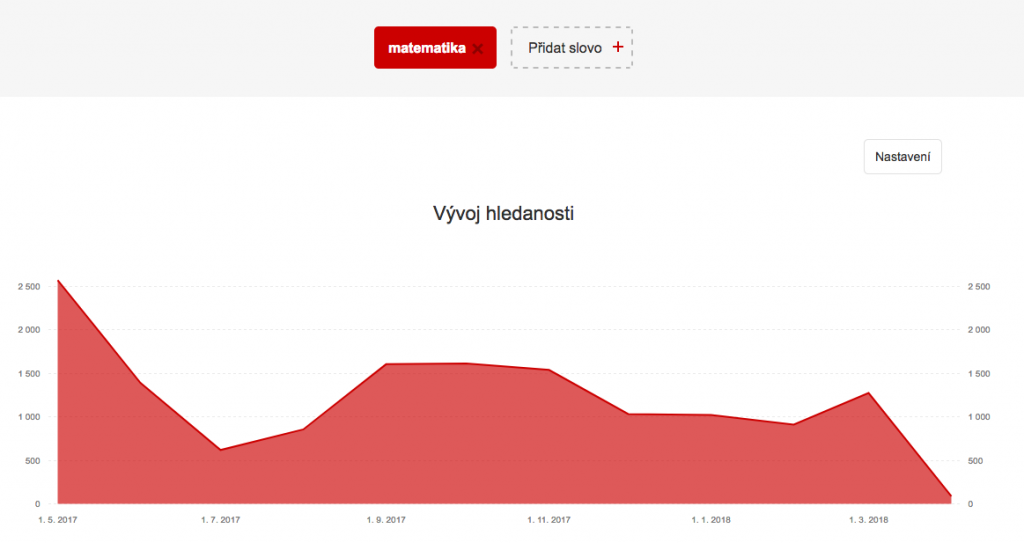
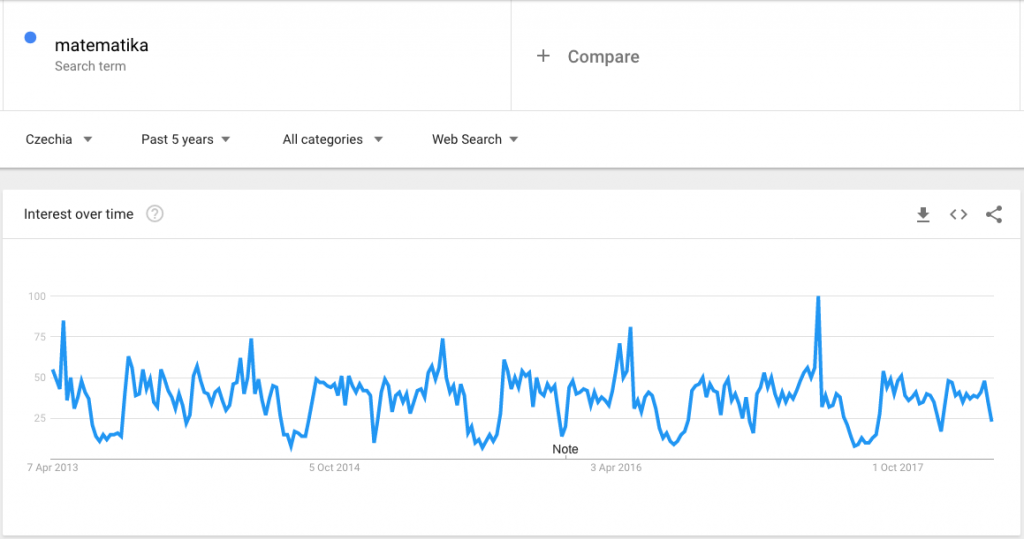
Google Trends shows a nice periodicity of the searches. Searches for ‚math‘ jump up with the start of the school year after summer holidays. The peak appears mostly when there are state exams on high schools.
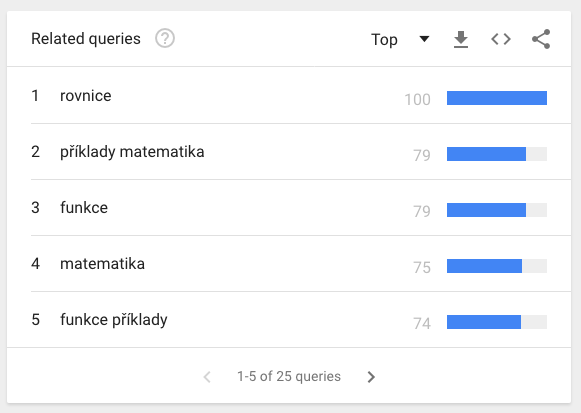
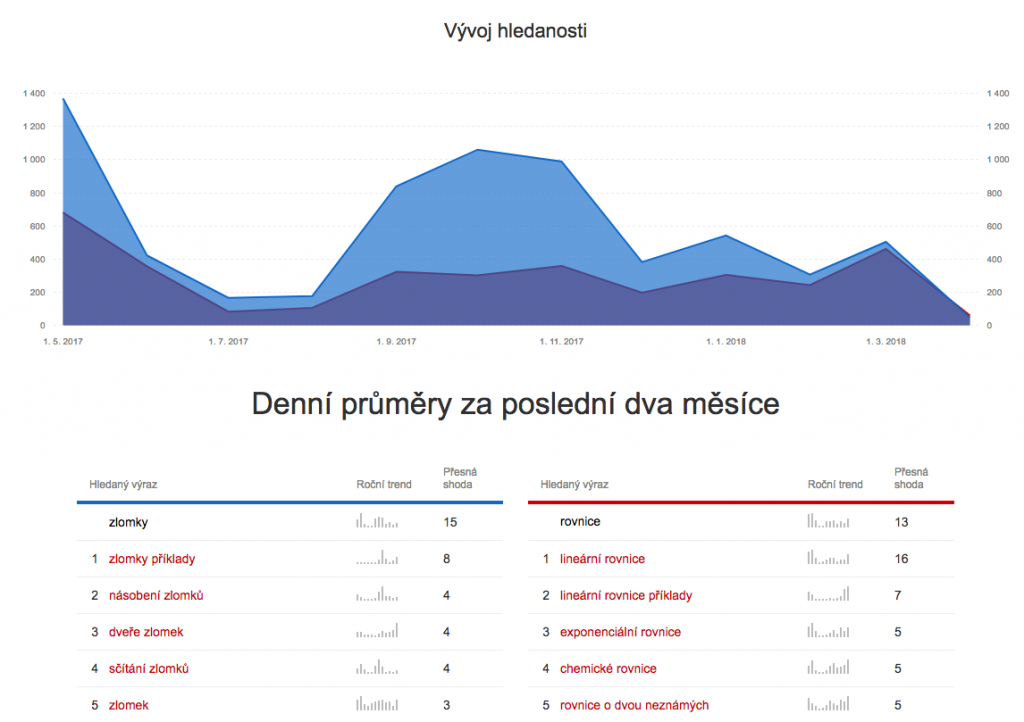
How to get to the math concepts and their difficulty? My idea was that those who need to learn something will try to train it. And so I’ve typed in ‘příklady’ (= math examples) and there was already something usable there. Google Trends showed me in top five related queries ‘rovnice’ (= equations) and ‘funkce’ (= functions). Seznam stats revealed among top five related queries ‘zlomky’ (= fractions), ‘lineární rovnice’ (= linear equations), and ‘dělení dvojciferným číslem’ (= division by two digit number). Apart from using this way to find math concepts to compare I’ve looked as well into learning plas such as this one for elementary schools and high schools.
I was playing with the tools showing the trends. I was trying different inputs – not only the keywords mentioned above but as well terms like ‘multiplication’, ‘division’, ‘combinatorics’, ‘geometry’ etc. It was not really easy to get a good formulation of the search terms – as many words might be used in another context outside of mathematics. This limitation might have biased my search. Anyway, it occurs to me that the three “problematic” concepts might be ‘fractions’, ‘equations’, and ‘functions’. I’ve used directly these three words at first. For Seznam ‘fractions’ and ‘equations’ worked well showing mostly mathematical terms in the top 5 related queries. The term ‘functions’ was of course used in mutliple domains (such as health), but the top related query was ‘goniometrické funkce’ (= goniometric functions). Seznam showed that ‘fractions’ were searched the most.
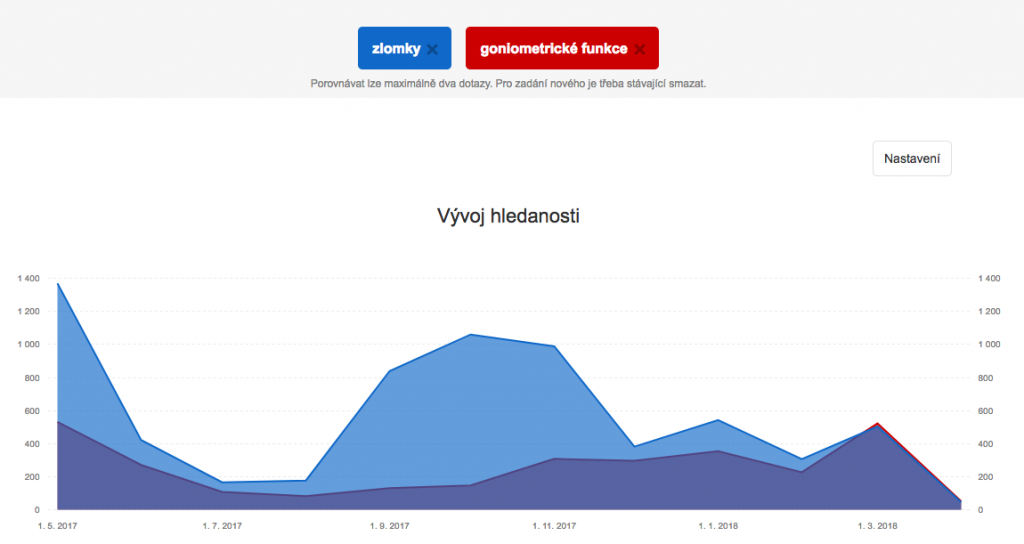
Google Trends shows it a bit differently. As the term ‘functions’ is ambiguous I’ve added to the term czech word for ‘examples’. The outcome is that from Google points of view the ‘equations’ and ‘functions’ are causing some problems and the ‘fractions’ are less problematic.
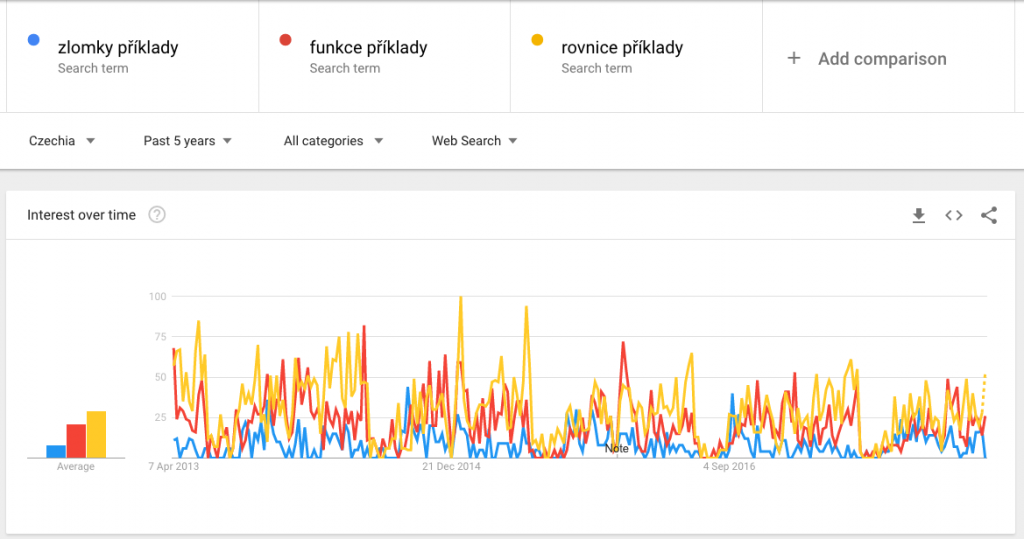
Let’s wrap up this short excursion to the search trends tools. We’ve uncovered some top searched math concepts – I’d say that it might show how many students are trying to grasp them. I admit that I could have made some flawed step in my “research”, but in general the thought of using the terms pupils search for in education could be useful. Maybe it can suggest in which direction we need better didactic methods, tools, videos etc.








